The Importance of Using a VPN
With more and more business activities going digital, internet security continues to become a growing concern. Keeping online activity secure requires more than just internet security software. Have you ever taken note of the number of digital traces left behind when you're simply surfing the web? Device type, location, IP address and more - all this information can be accessed by third parties. A virtual private network (VPN) has become a must have for businesses and individuals alike. VPN servers can be located in multiple countries providing anonymity. High-capacity VPNs allow for a large volume of traffic on the network. ...
Endpoint Protection is Essential For Your Business
Protect Your Business from Ransomware with Endpoint Security in San Antonio TX
Endpoint protection is essential for any business that relies on computers and networks. By definition, endpoint protection includes "the strategies and technologies used to secure the devices that connect to a network." This can include laptops, smartphones, tablets, and other internet-connected devices. In today's business world, it's essential to have a reliable endpoint protection solution in place to help protect your data and keep your operations running smoothly. Why Endpoint Protection is so Vital for Businesses: 1. Data Security Sensitive data is often stored on endpoint devices, making them a prime target for malware and hacker attacks. Endpoint protection helps ...
Why Your Business Needs a Plan for Data Backup and Recovery
The implementation of an online backup policy enables you to guarantee that your company will be able to continue operations promptly and effectively in the incident of something unexpected that ceases operations, there is a catastrophic event on the premises, you are the target of a ransomware attack, or there is some other occurrence that poses a risk to the accessibility and authenticity of your records. This article discusses the need for organizations to implement data backup and recovery plans. Time is of The Essence The ability to swiftly recover from a catastrophe, cyberattack, or devastating mistakes is just as ...
Business Continuity and the Vital Role it Plays in Success
How Business Continuity Protects Houston TX Companies from Disruptive Events
In today’s world, businesses can no longer depend solely on the four walls of their building for success. With ever-updated technology and rapidly changing business environments, managing a business has become about more than just the physical presence of that one location. Business continuity is not just about having a backup plan to help your company in a disaster; that’s only one part. It also means thinking and planning for anything that could happen with your company to stay ahead and successful. Business continuity planning involves many aspects, such as identifying critical business functions, assessing risks and vulnerabilities, and developing ...
Use Co-Managed IT to Transform Your Business
It is an essential part of today's business. You rely on technology to run your company, but your IT department might differ from what you need. Co-managed IT is a new and innovative way of providing your company with the IT services it needs to thrive. Co-Managed IT can transform your business in the following ways: 1. Improving Efficiency and Productivity Co - Managed IT services put an end to your business's struggle with technology. Managing your own IT service, mainly if you have limited resources, can be stressful, challenging, and inefficient. By outsourcing the management of your IT department ...
Social Engineering Attacks and How to Stay Safe
Secure and Maintain Business Continuity in Houston TX Against Social Engineering Attacks
Social engineering is a type of attack in which an individual or group of attackers uses deception and manipulation to trick users into giving them access to sensitive information, rights, or resources. These attacks are difficult to detect because they target human behavior rather than computer systems. Social engineers use various tricks and techniques to manipulate people into giving up confidential information or performing actions that are against company policy. Social engineering attacks are a constant threat for businesses of all sizes and can target any employee with access to sensitive information, including receptionists, vendors, contractors, and suppliers. To avoid ...
VoIP: 5 Ways it Can Help Your Business
Tips From Your Experts in San Antonio VoIP
Voice over Internet Protocol is a technology that allows voice communications to be sent via the internet rather than a conventional phone line and is often used by businesses looking to cut costs and save time. Here are five ways VoIP services in San Antonio can help your business. 1. Complete Scalability VoIP systems are very scalable. Whether you are planning to scale up or down, sooner or later, you can do it easily with VoIP. You can start with whatever size system you need and scale the size of it as your business grows without having to buy new ...
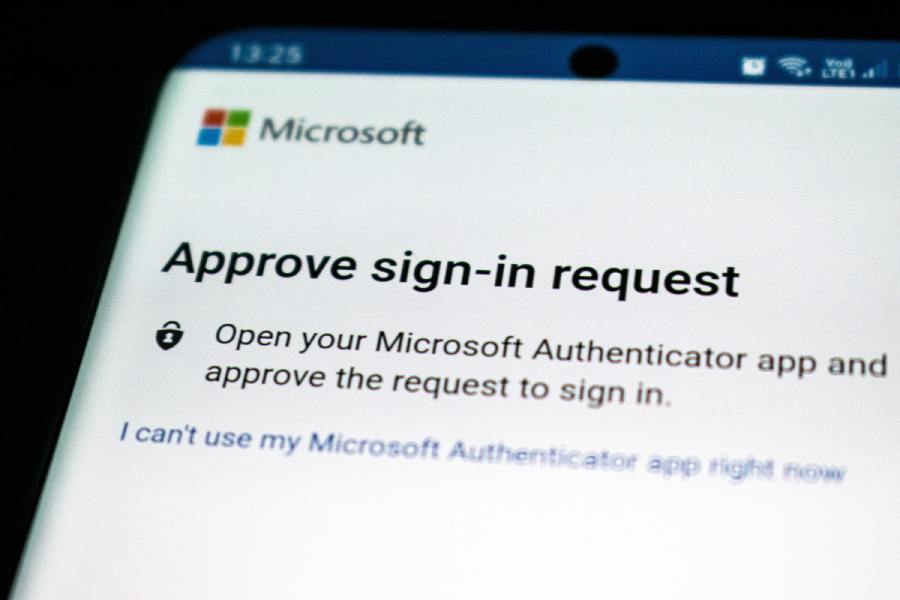
MFA: What Is It, and Why Use It?
MFA has many benefits, but most people use it to prevent unauthorized logins. This security measure offers many layers of protection, such as locking access to devices after several failed login attempts or requiring that the password match a client's PIN or other type of credentials. What is MFA? Multi-factor authentication, also known as MFA, refers to a security protocol requiring users to provide multiple pieces of evidence to log into a system successfully. This non-repudiation approach ensures that no one can access protected areas without authenticating their identity. Generally, MFA means adding a second form of authentication unrelated and ...
5 Easy Ways to Maintain Cybersecurity
Cybersecurity is a hot topic in the world of IT. You can’t watch a newscast without hearing about hackers, hacking, or stolen data. It’s easy to see why people are nervous every day, there are more and more issues with our security online. But we don’t have to be scared! Some good ways to combat this problem and ensure you stay safe in the digital world. Here are some five easy tips for maintaining Cybersecurity. 1. Keep Your Software up to Date One of the first things you should do is update your software. There are several ways to keep ...
The Many Ways that Cloud Computing Contributes to Productivity
Primer From Your Experts in cloud services in San Antonio
As businesses continue to embrace new technologies, the demand for business productivity solutions has increased exponentially. Organizations need ways to leverage technology and cut down on the time it takes to manage IT operations. Businesses that have a formal, structured business processes are often faster and more efficient than their counterparts. To improve business productivity, companies must eliminate unnecessary tasks and focus on activities that lead to results. The most common areas in which business productivity can be improved include collaboration, data management, analytics, and security. This blog discusses various ways in which cloud computing in San Antonio TX can ...
Categories
Recent Posts
- Network Builders IT Ranked on Channel Partners 2025 MSP 501—Tech Industry’s Most Prestigious List of Managed Service Providers Worldwide
- Staying Ahead of Technology Trends with Managed IT
- Managed IT Services and Support for Small Businesses
- Mitigating Cybersecurity Risks in The Supply Chain
- Choosing a Managed IT provider for Your Business